
Service Description
- Cloud-Bricks New Generation Firewall integrates the famous SNORT system in order to perform real-time traffic analysis and threat detection.
- This system is able to detect network attacks and
vulnerability exploits. Working in conjunction with the system
firewall it can generate alerts or even block attacks based on a
preconfigured set of rules. It works in a similar way to
Antivirus software for network packets.
- Cloud-Bricks Web Management Interface also integrates SNORBY, an easy to use Web system useful to browse SNORT generated alerts and monitor your network traffic health.
Snort Rules
The Intrusion Prevention System works based on a set
of rules files which contain all the threats definitions.
The SNORT system provides 3
different set of rules:
- Community
rules: Available for free for every one.
- Registered user rules: Available for free only for users registered at snort.org
- Subscriber rules: High-security rules with the latest updates, available only for paying users.
The Cloud-Bricks system comes with SNORT preconfigured with
Community rules only.
If you want to use the "Registered User Rule set", please Sign
Up at snort.org, get your oink code and contact
our support team.
If you want to protect your system with the most updated threat definition rules and receive support for snort, you may become a snort subscriber. Our support team will configure your SNORT system with the Subscriber Rule Set.
First time usage
In order to use the SNORBY system, some adjustments must be done
when logging in for the first time.
1- Access the SNORBY interface by navigating to Firewall ->
SNORT I.P.S in the left menu.

The default login is "snorby@snorby.org" and the default password is "snorby".
2- The SNORBY dashboard screen appears, please pay attention to the message "The Snorby worker is not currently running"
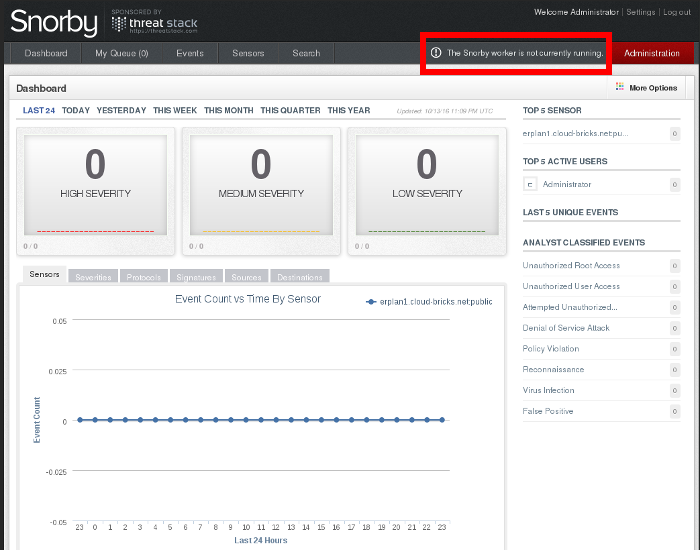
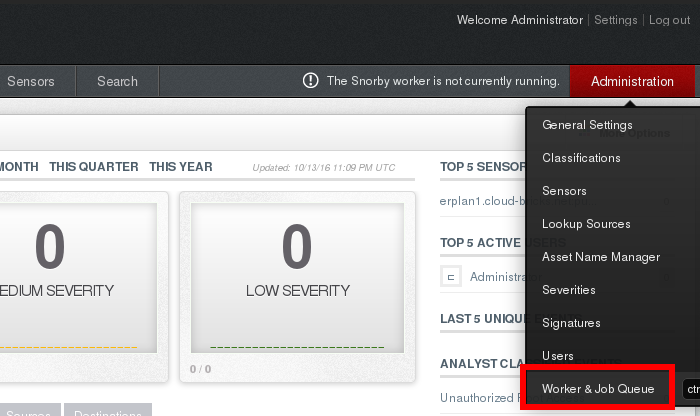
3- We need to start the Snorby Worker Process, in order to do so, please select the "Worker & Job Queue" option from the "Administration" menu:
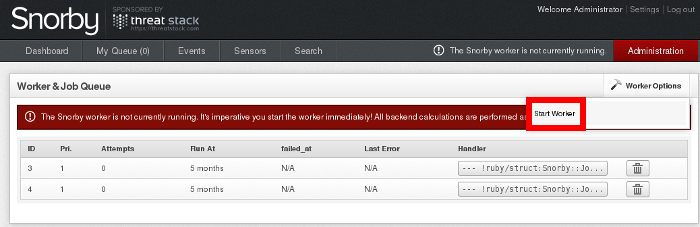
4- In the "Worker & Job Queue" page, please select the "Start Worker" option from the "Worker Options" menu.
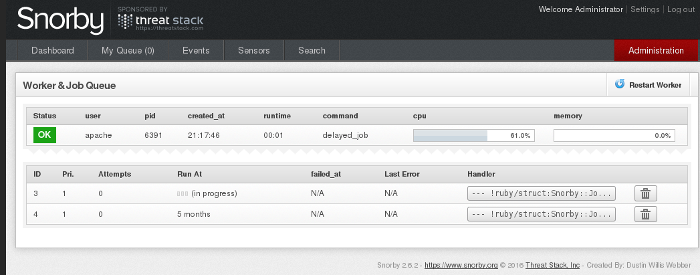
A green "OK" icon will confirm that the worked process has been started:
5- Now its time to configure your email, password and Time Zone:
The configuration page will appear when clicking on the "Settings" link in the upper right corner of the screen.
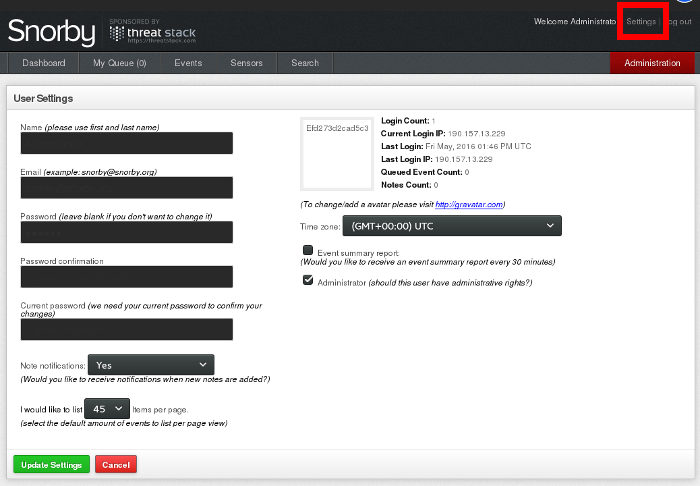
6- Please configure your actual email address and an easy to remember password to access the Snorby interface.
- Do not forget to update also your Time Zone so you can see the alerts with the right configuration.
- The first time you perform this configuration the current password is "snorby".
- After pressing the "Update Settings" button, you are done.
- The Snorby interface will show you any alerts of threats detected by the Snort IPS system.
Configuring your Virtual Machine to use the IPS system
In order to actually make the Intrusion Prevention System to scan
your virtual machine network traffic, you will have to include
some "IPS Filters" in your Firewall rules.
What to do in case of attack
- If you see some suspicious activity, alerts or attacks in the Snorby database, you need to identify the IP Address where the attack comes from.
- The Snorby interface will provide you a link to a web site with an explanation of the rule that was activated.
- If you are able to confirm this is not a false positive, you may want to block the attacker's IP Address using the Black List Firewall feature.
- Our support team may be able to help, but keep in mind that if
you need specific support for snort, you need to become an snort
subscriber.